Demo Request
See how 1000+ leading companies are screening against the world's only real-time risk database of people and businesses.
Request demoIn a data-driven financial landscape, cybercrime has become a significant concern for regulators and institutions alike, with criminals exploiting computer systems and online financial services to perpetrate money laundering, fraud, and other crimes. The cost of cybercrime money laundering is expected to reach around $10.5 trillion by 2025.
The Covid-19 pandemic exacerbated the threat posed by cybercrime and money laundering methodologies. With increased online financial activity and changes in customer behavior, criminals could target vulnerable individuals and institutions more easily and take advantage of regulatory blind spots.
Given the threats and the potential for significant penalties, banks, financial institutions, and other obligated entities should ensure that they understand the compliance risks they face and be prepared to deploy a suitable cybercrime and money laundering response.
Cybercrime is any illegal activity that involves a computer, the internet, or a networked device. With the emergence and growing ubiquity of online commercial and financial services (especially since the Covid-19 crisis), criminals have had greater opportunities to derive profits from online fraud and theft and, with that, a greater need to conceal the source of their illegal funds.
Computers and computer systems offer money launderers a degree of anonymity and the opportunity to move illegal funds quickly between accounts while avoiding the customer due diligence (CDD) and transaction monitoring checks that conventional anti-money laundering and combatting the financing of terrorism (AML/CFT) systems would normally impose.
Cybercrimes can be separated into two categories:
In November 2022, the Financial Crimes Enforcement Network (FinCEN) published a Financial Trend Analysis report on ransomware trends between July 2021 and December 2021. The analysis found that reported ransomware-related incidents increased by over 50 percent from 2020. Additionally, in the first half of 2022, it is estimated that 236.7 million ransomware attacks occurred, with an average cost of $1.85 million per incident.
Emerging cybercrime typologies and methods that are increasing include:
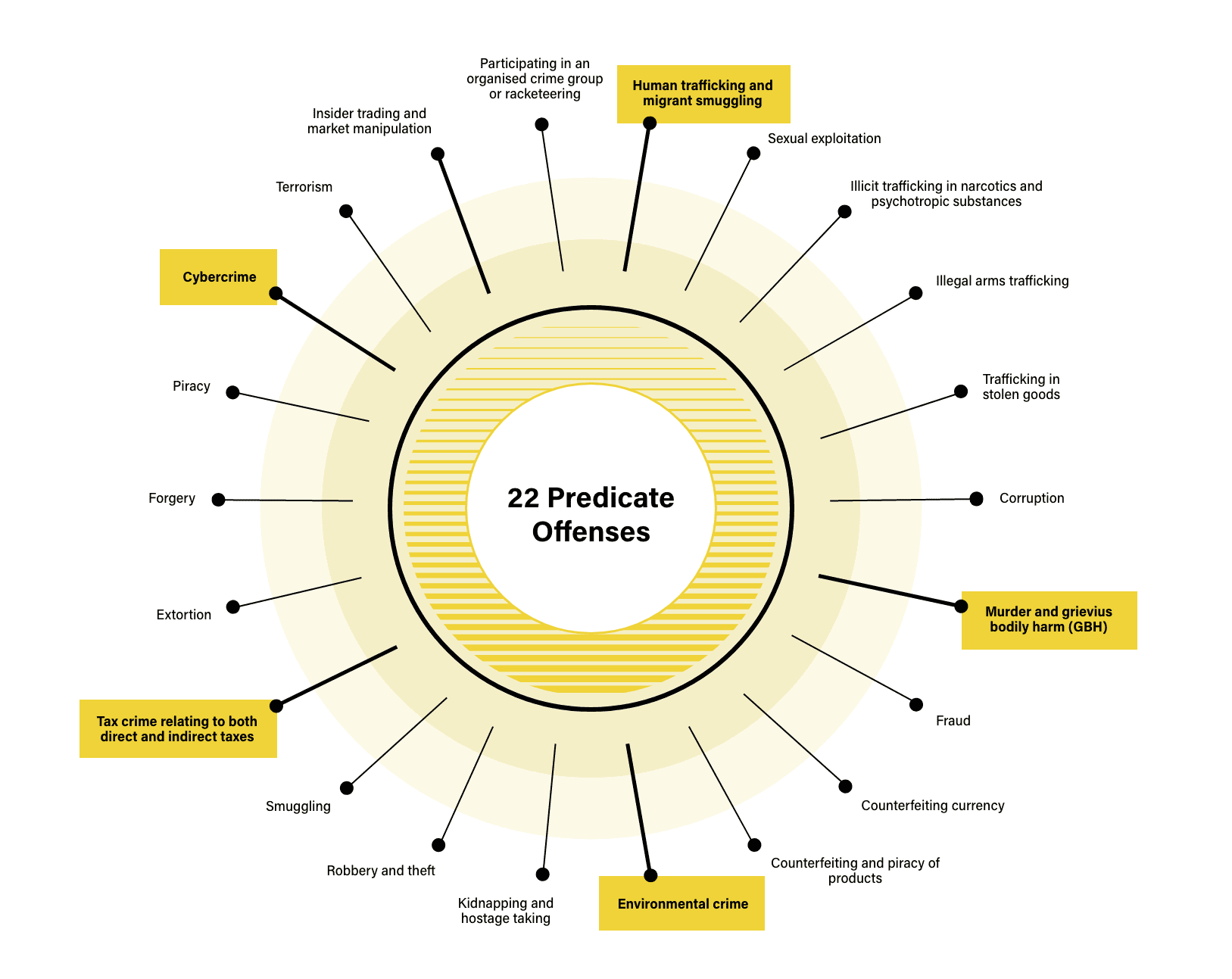
Cybercrime is considered a predicate offense because it generates illegal proceeds that need to be disguised by laundering before they can be entered into the legitimate financial system. The European Union’s 6th Anti-Money Laundering Directive (6AMLD) codifies this by including cybercrime in its list of 22 money laundering predicate offenses, joining existing predicate offenses like human trafficking, drug trafficking, counterfeiting, and theft.
Cyber laundering is when criminals use the internet to establish anonymity or non-traceability for laundering money.
Two of the most common types of cyber laundering are:
Some of the most popular methods used in cyber laundering include:
Cybercrimes often exhibit ‘red flag’ characteristics that can aid firms in detecting and preventing money laundering and in enhancing their compliance performance.
Since the COVID-19 pandemic, cybercrime has increased by 600 percent. In response, the Financial Crimes Enforcement Network (FinCEN) released a series of advisories calling financial institutions to be particularly vigilant for COVID-19-related attempts to launder money.
With the FinCEN advisories in mind, red flags that indicate cybercrime money laundering include:
Under Financial Action Task Force (FATF) recommendations, banks, financial institutions, and other obligated entities must put risk-based AML/CFT programs in place to deal with the AML/CFT threats that they face from cybercrime. In practice, this means that firms must conduct risk assessments of their customers and deploy a proportionate AML response. In the context of cybercrime, this means that firms must work to identify their customers and to monitor their transactional behavior on an ongoing basis with the following AML/CFT measures and controls:
It is vital that compliance staff report cybercrimes by filling in Suspicious Activity Reports (SARs). FINCEN advises any professional detecting a cybercrime to use the key term “CYBERFIN-2021-A004” and select SAR field 42 (cyber event).
See how 1000+ leading companies are screening against the world's only real-time risk database of people and businesses.
Request demoOriginally published 24 February 2021, updated 14 June 2023
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2024 IVXS UK Limited (trading as ComplyAdvantage).