

Following February’s plenary, the Financial Action Task Force (FATF) issued two new reports related to countering ransomware financing. One report analyzes the methods cybercriminals use to carry out attacks and the techniques they use to launder ransom payments, while the other focuses on potential risk indicators. Both sets of guidance aim to enhance the detection and prevention of suspicious transactions relating to ransomware.
A core focus of the February plenary was the increasing scale of ransomware attacks, particularly highlighting the misuse of virtual assets (VAs) allowing criminals to escape undetected with large amounts of money. According to the IBM X-Force Threat Intelligence Index, in 2022 Asia-Pacific saw the highest number of cyberattacks for the second year in a row.
The FATF’s new reports are the result of research carried out by the global watchdog to better understand the challenges at large.
Common Methods and Trends
When presenting its 2022-2024 objectives in July 2022, the FATF noted that many countries are struggling to stop or contain cyber-enabled schemes. Our 2022 and 2023 global compliance surveys echo this challenge, with cybercrime emerging as the top predicate offense of concern for compliance teams two years in a row.
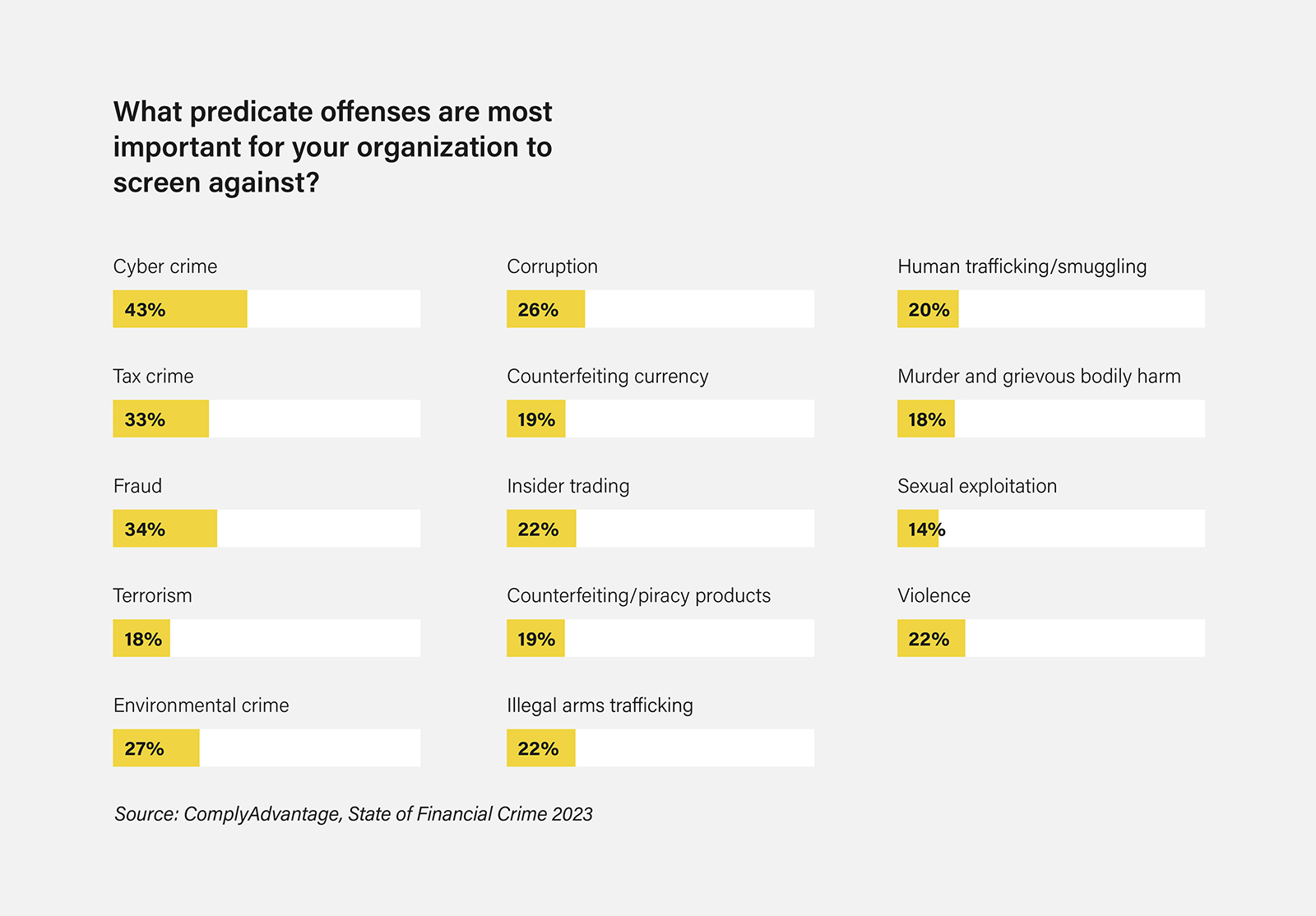
And it’s clear to see why. According to the FATF, recent estimates report a fourfold increase in ransomware payments in 2020 and 2021, compared to 2019, owing to new tactics and techniques being utilized by criminals.
Common ransomware methods and related trends identified in the report include:
- Mixers or tumblers – used to obfuscate the connection between the wallet address sending VAs and the addresses receiving VAs
- “CoinJoin” transactions – where multiple senders and recipients of funds combine their payments in a single transaction
- Anonymity-enhanced cryptocurrencies – used in conjunction with privacy-enhancing technologies such as mixers, ring signatures, stealth addresses, and ring confidential transactions
- Monero – this VA is increasingly being requested by cybercriminals, despite Bitcoin remaining the most commonly used VA in ransomware
- Chain-hopping – used to convert ransom payments from one VA (usually Bitcoin) to another (increasingly stablecoins), before exchanging funds into fiat currency
- Money mules – used to convert ransom payments back into fiat currency by using off-ramps
- Over-the-counter traders – these centralized VASPs are often used to cash out illicit proceeds
- High-risk jurisdictions – cybercriminals send the VAs to high-risk countries with weak or non-existent anti-money laundering and counter-terrorist financing (AML/CTF) controls to convert them into fiat currency.
Compliance staff should note that many of the above methods and trends can be categorized as general crypto money laundering typologies. In this context, concealing ransom payments is the cybercriminal’s goal.
Proposed Actions
In light of the methods used by cybercriminals to carry out ransomware attacks, the FATF provided a list of practical actions countries should take to enhance their ability to disrupt financial flows related to the rising cybercrime type. Good practices include:
- Implementing relevant FATF Standards, including on VASPs, and enhancing detection
- Promoting financial investigations and asset recovery efforts
- Adopting a multi-disciplinary approach to tackle ransomware
- Supporting partnerships with the private sector
- Improving international co-operation
Potential Risk Indicators
The list of risk indicators outlined by the FATF complements those provided in previous guidance on virtual assets red flag indicators published in September 2020. To provide maximum clarity and help public and private sector entities identify suspicious activities related to ransomware, the second report separates the risk indicators by perspective. First, the report lists indicators to help firms identify ransoms paid by victims:
- Outgoing wire transfers to cybersecurity consulting firms that specialize in ransomware remediation
- Unusual incoming wire transfers from insurance companies that specialize in ransomware remediation
- A customer seems anxious or impatient with the amount of time taking for a payment
- Purchases of or transfers involving anonymity-enhancing cryptocurrencies
- A new customer purchases VAs and transmits the entire balance of their account to a single address
Second, the FATF highlights indicators to help firms detect a criminal account that has received (or is receiving) a ransom payment:
- Transactions involving anonymity-enhancing cryptocurrencies
- Transferring VAs to mixing service
- The use of an encrypted network
- Immediate withdrawal after converting funds to VAs
- Customer information shows that the customer holds an email account known for high levels of privacy such as proton mail or Tutanota
- A high volume of transactions from the same bank account to multiple accounts at a VASP
The FATF notes that a single risk indicator may not warrant suspicion of a ransomware payment on its own. Nor will a single indicator necessarily provide a clear indication of such activity. However, should compliance staff identify any of the indicators highlighted above, teams should undertake further monitoring and examination as appropriate.
Key Takeaways
Managing the risk of ransomware is becoming increasingly complex. To better protect their customers and their firm’s reputation, compliance teams should consider enhancing their cyber defenses and practice increased levels of cyber hygiene. The new ransomware methods and trends identified by the FATF should also be reviewed against firms’ AML/CTF controls, ensuring any gaps are addressed in accordance with the firm’s risk appetite.
To learn more about the key takeaways from February’s plenary session, read our coverage here.
Spotlight on Financial Crime
Explore the trends shaping today’s financial landscape and their implications for the year ahead.
Download nowOriginally published 23 March 2023, updated 12 February 2025
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2026 IVXS UK Limited (trading as ComplyAdvantage).
