Get tailored risk insights
Verify customers with live Sanctions, PEPs, and Adverse Media data and insights for free.
Try NowOne of the ways the US punishes violations of international law, human rights abuses, and other state-sponsored criminal activities is by imposing economic sanctions against countries, entities, and individuals. The OFAC sanctions regime is implemented and enforced by a dedicated branch of the Treasury Department – the Office of Foreign Assets Control (OFAC).
The Office of Foreign Assets Control (OFAC) supervises and implements economic sanction programs against countries and other entities – such as terrorist organizations or drug traffickers – to help achieve US foreign policy and national security goals. In its supervisory role, OFAC ensures that US entities and individuals comply with sanctions regulations. It may impose fines where it discovers that violations have occurred.
Operating under the Office of Terrorism and Financial Intelligence (TFI), OFAC is primarily composed of lawyers and intelligence targeters. While many of OFAC’s targets are set by the White House, the majority of individual cases are developed in light of investigations by OFAC’s Office of Global Targeting (OGT).
There are two types of sanctions regulation, primary and secondary sanctions:
OFAC primary and secondary sanctions generally impose the following restrictions and prohibitions:
OFAC sanctions are implemented in two ways:
The targets of OFAC sanctions are designated on OFAC sanctions lists, which are updated as new designations are added and withdrawn. OFAC may grant licenses that exempt certain US firms from sanctions restrictions under particular circumstances. Firms should apply to OFAC to obtain a general OFAC license or submit a written request for a specific OFAC license.
OFAC lists contain information about the individuals, companies, countries, or groups being targeted, as well as information about the sanctions they are subject to. The two main OFAC sanctions lists are:
Other US sanctions include the Sectoral Sanctions Identifications List (targeted at Russia), the Foreign Sanctions Evaders List, the more specific non-SDN Palestinian Legislative Council List, and the Iranian Sanctions List.
OFAC sanctions regulations can vary greatly by country. While some countries, such as Belarus, Libya, and Sudan, are subject to sanctions that prohibit transactions related to activities with specific parties, other countries face more comprehensive restrictions. These include:
For in-depth information of specific sanctions programs, OFAC issues interpretive guidance and FAQ sheets pertaining to various sectors. Such as:
What’s the update: On August 23, 2024, OFAC significantly expanded its Specially Designated Nationals and Blocked Persons list (“SDN List”), updating 402 entities. Of these updates, 391 represent newly designated entities, targeting Russia’s metal, mining, and technology sectors across 16 jurisdictions. These actions underscore the U.S. government’s efforts to disrupt Russia’s international supply chains and prevent the circumvention of sanctions.
OFAC’s press release highlighted the extensive transnational networks designed to evade sanctions. These networks involve Russian financial institutions, asset management schemes, and suppliers of foreign electronic components crucial for Russia’s military advancements. They also involve the relocation of services to Russian nationals.
Notably, several entities designated by OFAC were also identified by the Bureau of Industry and Security for actions contrary to the national security or foreign policy interests of the United States.
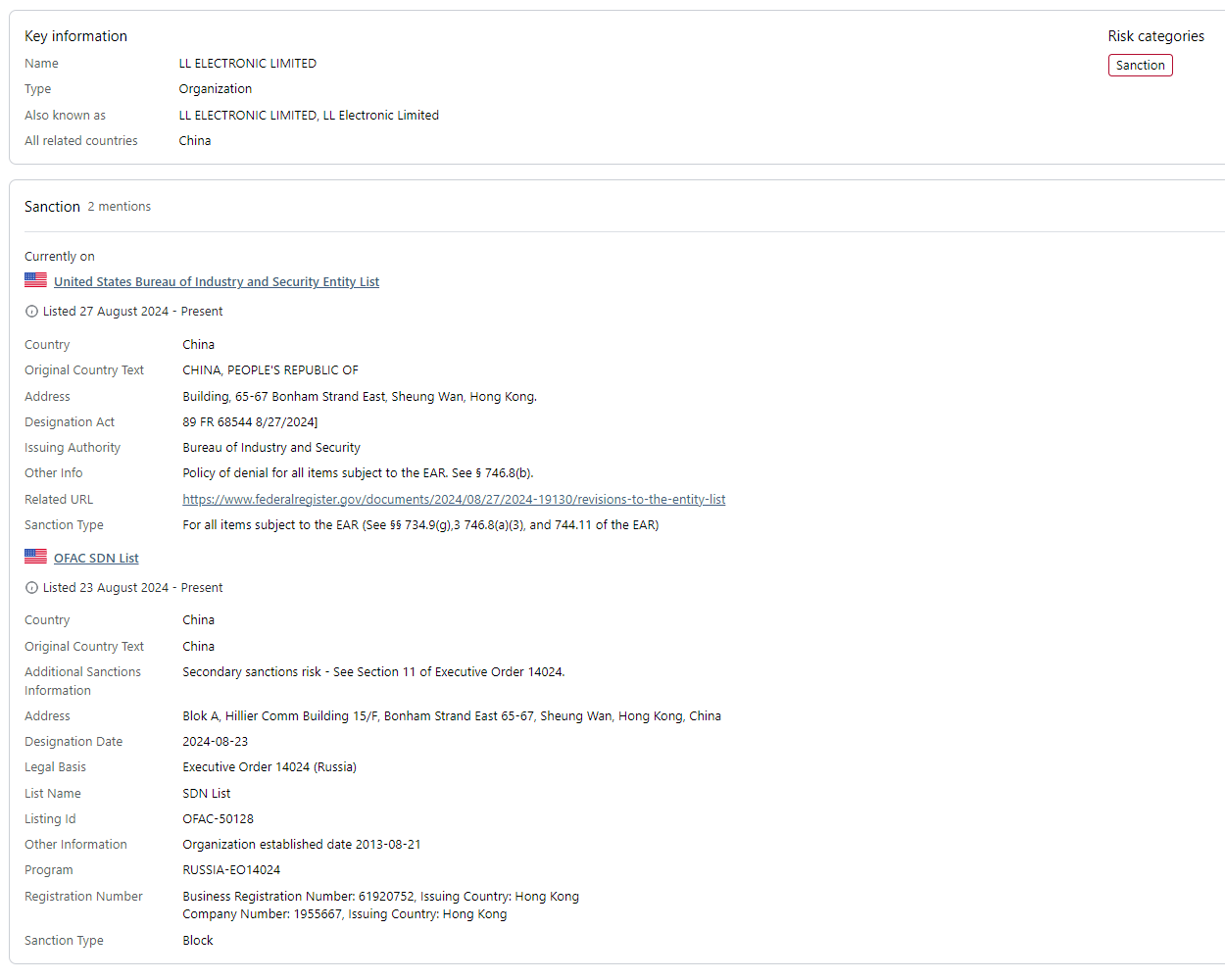
For example, LL Electronics Limited, a Hong Kong-based company who shipped electronic integrated circuits and multilayer ceramic capacitors to U.S.-designated Russian electronic component importer Limited Liability Company Kvazar.
As sanctions grow in volume and complexity, the challenge of maintaining compliance has never been greater. Companies must rigorously screen their clients and transactions against the latest updates to avoid potential enforcement actions. This task, while daunting, is made manageable by ComplyAdvantage’s rapid response capabilities.
In less than two hours of OFAC’s announcement, ComplyAdvantage validated and made all 400+ updates available to our clients. This swift action ensures that businesses using ComplyAdvantage’s financial crime intelligence can maintain up-to-date compliance and mitigate risks effectively, even as the regulatory landscape evolves.
All individuals, banks, financial services companies, and other obligated institutions operating under US jurisdiction must comply with OFAC sanctions. For banks and other financial services firms, this means integrating an OFAC sanctions search into internal AML compliance programs and ensuring that new customers and clients are screened against the sanctions list before a business relationship begins.
OFAC considers sanctions non-compliance to be a serious threat to national security and foreign relations and, therefore, an OFAC sanctions violation. Consequently, those who breach OFAC sanctions without obtaining the proper license can face severe legal repercussions. Fines range up to $20 million, depending on the offense, and prison sentences can be as long as 30 years.
If in committing a sanctions violation, a party also violates the Trading with the Enemy Act, it may be penalized with a $65,000 fine per sanctions violation. For violations of the International Emergency Economic Powers Act, the fine increases to $250,000 per sanctions violation. Similarly, breaking provisions of the Foreign Narcotics Kingpin Designation Act can result in fines of up to $1,075,000 per violation.
Naturally, these numbers vary considerably depending on the specific crime committed and the number of times it occurred. The specifics of these sanctions also change very frequently, so it is crucial to stay up to date; this will allow you to ensure both that you are compliant and that you don’t unnecessarily limit your business activity by adhering to sanctions that have been revoked.
Firms must ensure new customers are screened against global sanctions and watchlists during the onboarding stage. Once a business relationship has been confirmed, and a customer risk rating applied, firms should review the account on an ongoing basis to stay up-to-date with any critical changes in the customer’s risk status. Ideally, sanctions and watchlist screening should be automated and synced with a firm’s data feed, case management system, and CRM.
Performing OFAC sanctions screening manually, can be administratively challenging, costly, and inefficient. Human error may also lead to inaccuracies and the risk of penalty fines. Using an automated sanctions and watchlist screening tool minimizes that risk.
AI and financial crime technology not only build accuracy into AML programs but helps firms quickly and efficiently achieve the compliance standards regulators as OFAC requires.
Verify customers with live Sanctions, PEPs, and Adverse Media data and insights for free.
Try NowOriginally published 21 June 2014, updated 16 September 2024
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2025 IVXS UK Limited (trading as ComplyAdvantage).