
Read our Guide to Customer Onboarding
Discover our guide to find out how to effectively manage challenges faced during the customer onboarding process.
Learn moreUnderstanding where customers have obtained the money that they are using to carry out transactions and make investments is an important part of the Know Your Customer (KYC) process and integral to AML/CFT compliance. As money launderers use increasingly sophisticated methodologies to conceal the source of illegal money, firms must work harder than ever to establish the source of funds and wealth. Practically, this means that firms must implement an array of KYC measures and controls, such as customer due diligence (CDD) and transaction monitoring measures, in order to protect both their assets and their customers, and to contribute to the global fight against financial crime.
In order to scrutinize source of funds (SOF) and source of wealth (SOW) it is important to understand the distinction between the terms.
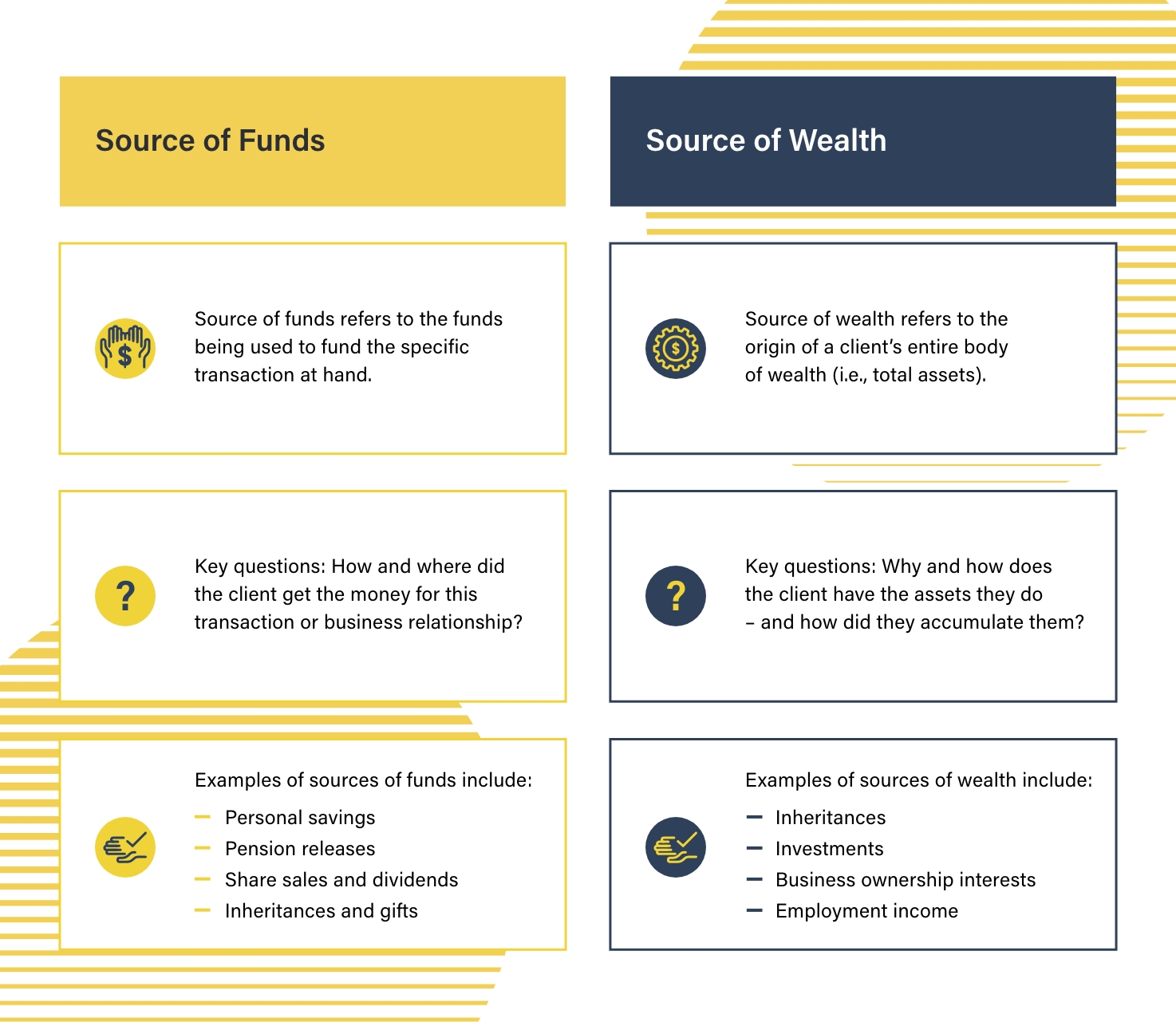
The source of funds (SOF) is the origin of a person’s money or financial assets. In establishing the source of funds, firms must seek to understand not only where funds came from (in terms of the account from which they were transferred) but the activity that was involved in generating those funds – for example, a source of employment, the sale of a house, or an inheritance.
Examples of sources of funds include:
The source of wealth (SOW) refers to the means by which a person has acquired their entire body of wealth. In establishing the source of wealth, financial institutions must ascertain why the client has the assets they do and how they came to accumulate them.
Examples of sources of wealth include:
While the source of funds may be more immediately pertinent to AML/CFT compliance efforts, both SOF and SOW should be considered when establishing a customer’s potential involvement in criminal activity. When a customer is flagged as ‘high risk’ and an enquiry into the origin of their funds is initiated, SOW may be used as a way to support a decision about SOF.

Discover our guide to find out how to effectively manage challenges faced during the customer onboarding process.
Learn moreSource of funds and source of wealth are crucial to the fight against money laundering and terrorism financing since both can be good indicators that customers are involved in criminal activity. In contexts where SOF and SOW do not match a customer’s risk profile, or established transaction activity, firms should use that information to inform their AML/CFT compliance response, and when submitting suspicious activity reports (SAR) to relevant domestic authorities.
An AML source of funds enquiry should involve the following measures and considerations:
Not all suspicious transactions and financial activities warrant source of funds enquiries and financial authorities do not recommend them for every suspicious incident. The Australian Transaction Reports and Analysis Centre (AUSTRAC), for example, points out that customer identification discrepancies and other identification concerns may be better resolved by triggering enhanced due diligence measures (EDD), rather than implementing an SOF investigation.
If there are concerns about a customer’s SOF, firms must be ready to take the necessary compliance steps to address the potential compliance risk. Depending on regulatory requirements, compliance responses to source of funds may include:
Where scrutiny of a customer’s SOF reveals suspicious activity, a firm should submit a suspicious activity report (SAR) to the relevant authorities. In the US, for example SAR should be filed with the Financial Crimes Enforcement Network (FinCEN).
In order to effectively establish SOF, firms must develop and implement suitable KYC measures in order to understand who their customers are, and what type of business they are engaged in.
Under the risk-based approach to AML compliance recommended by the Financial Action Task Force (FATF), those KYC measures should be proportionate to the risk that different customers present. This means that higher risk customers should trigger enhanced compliance measures, while lower risk customers may warrant simplified measures.
The KYC process should feature the following measures and controls:
Our annual report combines expert industry analysis with a global survey of 600 compliance leaders to offer a roadmap for 2025.
Download your copyOriginally published 12 October 2021, updated 22 January 2025
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2025 IVXS UK Limited (trading as ComplyAdvantage).