
The State of Financial Crime 2025
Packed with practical tips from our team of subject-matter experts, download our fifth annual report that explores the major trends and topics set to shape the year in compliance.
Download nowAML programs are driven by data. They rely on it to detect suspicious activities, identify potential risks, and ensure compliance with evolving regulatory obligations. But what kind of data is needed to help your compliance team see beyond the surface and make informed decisions about your customers and their transactions?
To help answer this question, this article will cover:
A main component of quality data is its comprehensiveness – not just the breadth and depth of information collected but also how seamlessly it integrates with other data points to enrich its information. When viewed holistically, comprehensive data allows firms to construct a full, accurate picture of potential risk, turning disparate pieces of information into insights that allow analysts to make informed decisions. This integration is necessary for generating meaningful outputs, such as real-time risk scores, which empower firms to take a risk-based approach to alerts.
On the other hand, gaps in data coverage can leave firms vulnerable. Missing or incomplete information may result in undetected instances of money laundering and regulatory breaches. For example, in 2023, a subsidiary of a major commercial bank was fined $25 million by the Financial Crimes Enforcement Network (FinCEN) for failing to fully integrate crucial customer data from the know your customer (KYC) process into its risk assessment and transaction monitoring systems. This data gap prevented the firm from detecting suspicious activity and filing suspicious activity reports (SARs) within the required timeframe.
Compliance failures like this often stem from siloed data and disparate platforms that fail to integrate various types of relevant AML data, a challenge identified as the major limitation for compliance leaders in our State of Financial Crime 2025 survey. In fact, the top three concerns revealed by compliance leaders were:
What are the main limitations to your organization’s current approach to financial crime detection?
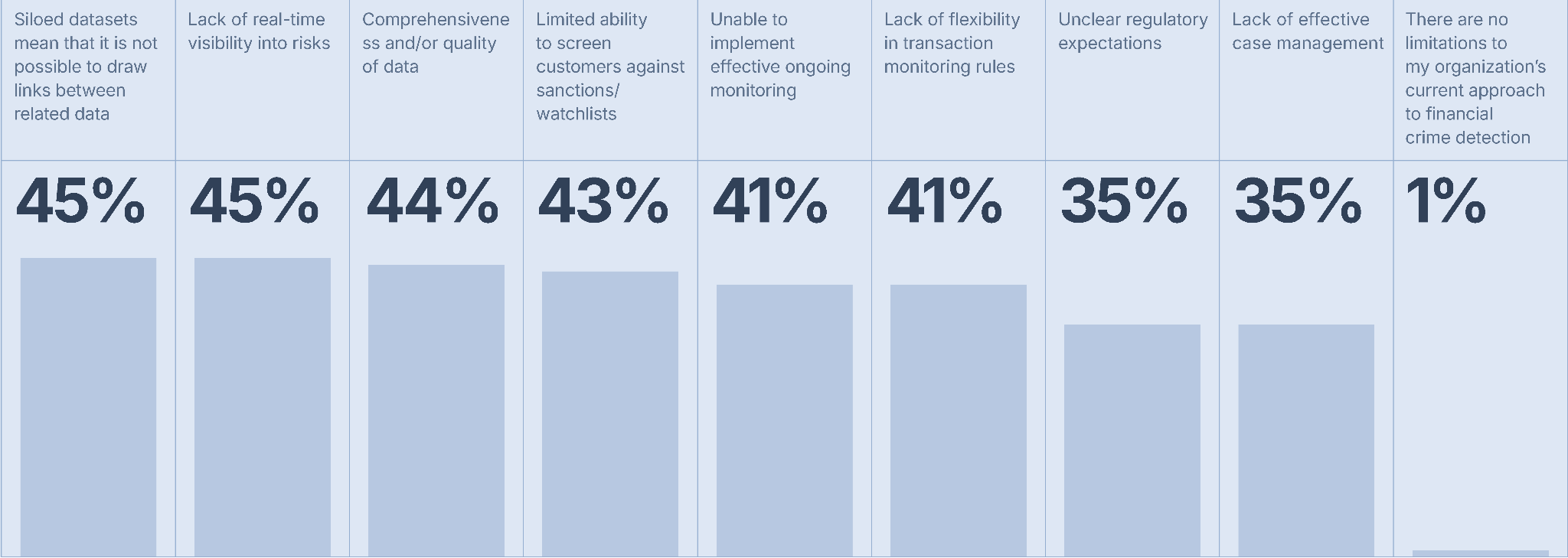
These issues highlight a critical problem: the inability to connect high-quality data and quickly draw inferences from it.
If your firm is actively looking to combat this challenge, understanding which AML data types are essential to creating a comprehensive risk picture is a good place to start.
While various data types are often used across multiple stages of the AML process, the table below shows how nine different kinds of data relate to some of the larger compliance activities that occur throughout the client lifecyle.
| Stage in the AML process | Data required | AML purpose |
| Customer onboarding | Customer information
BOI PEPs & RCA data Geographic risk data |
Customer identification, KYC/KYB onboarding, risk profiling: Used to verify customer identity, assess ownership structure, and identify higher-risk individuals like PEPs or RCAs. |
| Sanctions screening and risk checks | Sanctions & watchlist data
Adverse media |
Sanctions screening, name matching, and customer risk assessment: Ensures customers, payments, and counterparties are not on sanctions lists or linked to negative media or high-risk individuals like PEPs. |
| Ongoing monitoring | Transaction data
Behavioral data |
Transaction monitoring & anomaly detection: Tracks customer transactions and behavior to detect suspicious patterns, unusual activity, and deviations from expected behavior. |
| Historical review & investigations | Historical data | Audit trails and regulatory investigations: Provides a historical view of customer activity, profile changes, and past transactions to support audits and regulatory investigations. |
But what are the hallmarks of these data types? What does “good” look like in each case and what insights can typically be derived from the information provided? The next sections consider these questions in relation to each of the following:
Know your customer (KYC) regulations make up the foundation of AML compliance. The process begins with collecting accurate and comprehensive information directly from the customer. Without this initial step, the onboarding process may stall before it truly begins.
Key customer information typically includes:
Once this data is collected, your compliance team’s expertise comes into play. Meticulous verification of the provided information is essential to ensure its authenticity and identify any possible risk factors. In some cases, additional inquiries into the customer’s source of funds (SoF) or source of wealth (SoW) may be necessary to build a comprehensive risk profile.
Ultimate beneficial owners (UBOs) are individuals who ultimately own or control a company and benefit from its financial activity. However, identifying these individuals can be challenging due to complex ownership structures often designed to obscure their identities.
Key beneficial ownership information to collect includes:
The challenge lies not just in collecting this information but in interpreting it correctly. Your compliance team should be well-trained in recognizing red flags, such as unnecessarily complex structures or ownership chains that lead to high-risk jurisdictions. By thoroughly mapping out beneficial ownership, your team can better assess the risk associated with a business relationship and make informed decisions about customer onboarding and ongoing due diligence.
Due to their prominent public functions, PEPs are considered higher risk for potential involvement in bribery, corruption, or money laundering. This risk often extends to their family members and close associates. Effective PEP and RCA screening requires comprehensive and up-to-date data. While the process can be complex, focusing on key elements can significantly enhance the quality and usefulness of PEP-related information. The hallmarks of “good” PEP data include:
To learn more about what constitutes “good” PEP data, read the dedicated blog written by our Regulatory Affairs Practice Lead, Iain Armstrong.
Because some jurisdictions have comparatively weak AML/CFT legislation, are known to be offshore financial havens, or have high levels of corruption, drug trafficking, and other predicate crimes in money laundering, a potential customer’s location factors into their risk status.
While there is no definitive global approach to identifying high-risk geographic locations, if an entity has ties to a jurisdiction that features on lists such as the Financial Action Task Force (FATF) ‘black’ and ‘grey’ lists, it is enough for it to be deemed higher-risk.
Beyond FATF lists, your compliance team may consider data provided by:
Staying on top of sanctions and watchlist updates is a critical yet increasingly challenging task for compliance teams. With new sanctions designations being introduced at a rapid pace, your ability to access accurate and comprehensive data is essential for maintaining compliance. However, not all sanctions data providers offer the same level of quality, and gaps in data can lead to significant risks.
High-quality sanctions data can be evaluated using several key factors:

Packed with practical tips from our team of subject-matter experts, download our fifth annual report that explores the major trends and topics set to shape the year in compliance.
Download nowAdverse media information consists of negative news or content about individuals or organizations spread through various media channels. This includes:
However, when dealing with negative news screening, one of the main challenges analysts face is having to sift through vast amounts of data to identify relevant information. A major issue is the prevalence of irrelevant or noisy data. For example, searching for “Tiffany Palmer” on Google will generate over 70,000 results, even when using specific keywords like fraud or money laundering. Another challenge relates to keeping track of a customer’s risk information over time and assessing the quality and credibility of the data in question.
Adopting a machine learning (ML) approach to adverse media screening can help combat these challenges, giving your team access to unstructured data that has been pre-analyzed, categorized, and consolidated into comprehensive profiles. However, as with every other screening process, acquiring high-quality, relevant, and diverse data is crucial for training effective ML models. While various datasets exist, solving specific AML problems often requires millions of carefully curated training examples. Not every data provider will have access to or utilize such extensive datasets. In contrast, vendors that leverage their own proprietary data can offer enriched insights.
Transaction data largely consists of information referring to:
The Financial Action Task Force (FATF)’s recommendations emphasize the importance of capturing all relevant transaction data, including the originator’s and beneficiary’s details, to improve traceability. To ensure all information is complete for your risk analysis, make sure your teams are monitoring the quality of the transaction data they receive and are trained on the appropriate action to take when essential details are missing.
While transaction data provides the raw facts of financial activities, this data alone may not reveal the full picture of potential money laundering activities. Behavioral information, on the other hand, adds crucial context by analyzing patterns and trends in customer activities over time. Behavioral data typically includes:
When behavioral data patterns are analyzed, your team can then craft customized rulesets that align with your specific customer base and risk appetite. These tailored rules enable more accurate detection of suspicious activities while reducing false positives. For example, TransferMate was able to work with ComplyAdvantage to tailor-make a rule that would detect key behavioral indicators for child sexual exploitation. Additionally, after receiving key updates from law enforcement in the field, they were able to immediately refine the rule and account for behaviors indicating abuse of younger victims. With other solutions, making the change could have taken six months or more.
Historic data in AML screening is essentially a longitudinal view of customer interactions and financial activities over an extended period of time. It provides a consolidated, time-based perspective that allows compliance teams to:
Historic data is also vital during audits and regulatory investigations as it essentially acts as a log of your team’s decisions.
In AML compliance, “data retention” refers to the practice of storing customer-related data for a specified period of time. As well as providing evidence for any investigations, data retention also allows firms to monitor and analyze activity for potential money laundering or terrorist financing.
Depending on the jurisdiction in which your firm operates, the period of time companies have to retain customer data can vary. For example:
Strong data retention practices help ensure your team can meet its regulatory requirements, conduct effective investigations, and maintain accurate records for long-term compliance. Some key questions you can ask to assess a vendor’s data retention and governance capabilities include:
ComplyAdvantage is one of very few RegTech providers to hold its own financial crime risk data, alongside the software and UI layers. This means firms can access their full AML stack from one provider – no need to purchase data separately.
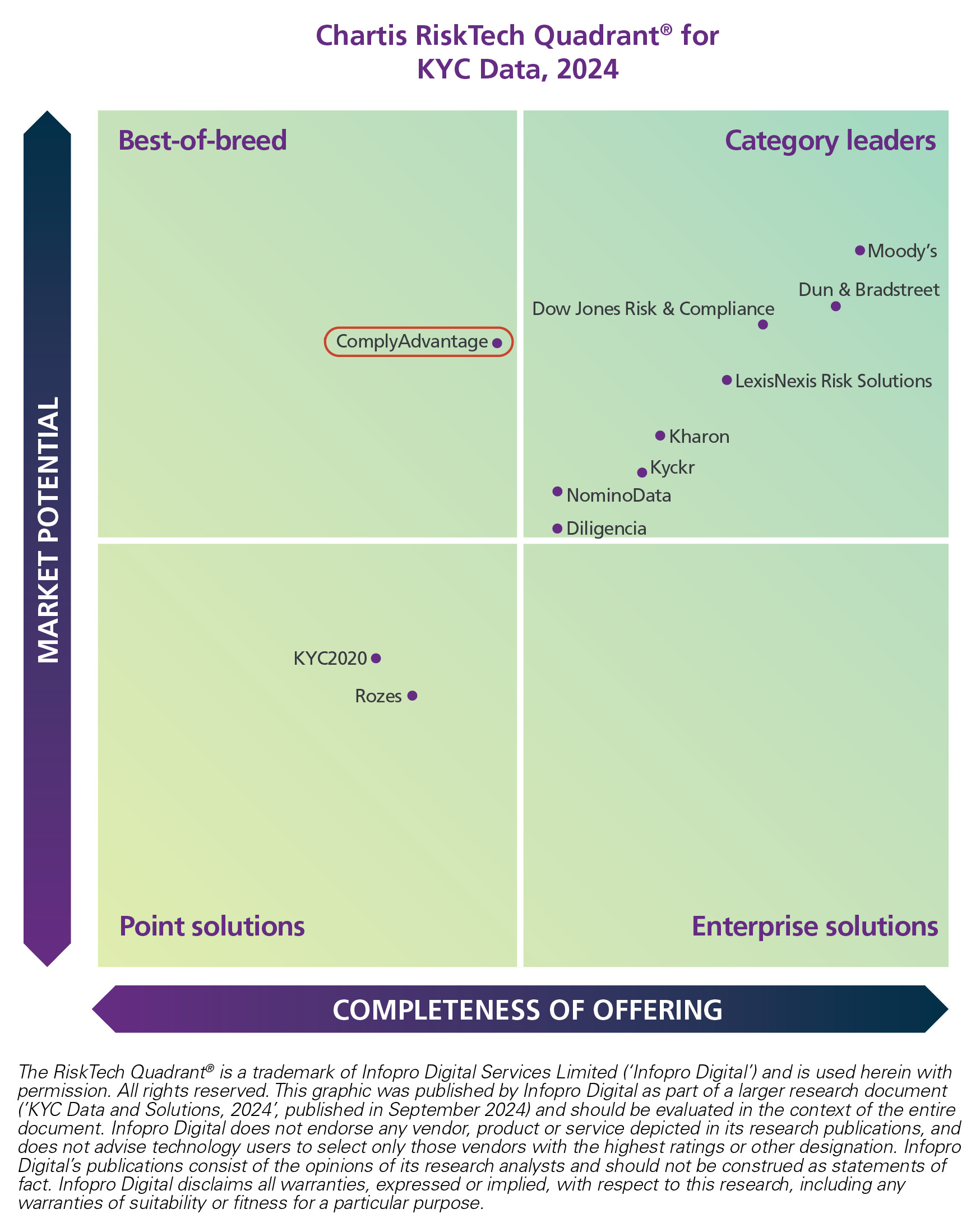
As a specialist in financial crime, we are experts in providing the sanctions, PEPs and adverse media data compliance teams need. Chartis’ latest analysis of the KYC Data market showed us as the sole ‘best-of-breed’ vendor, reflecting our specialist expertise in financial crime risk intelligence. Specifically, we were the only firm to receive best-in-class scores in both the ‘sanctions and watchlist data’ and ‘negative news and PEPs’ categories.
A cloud-based compliance platform, ComplyAdvantage Mesh combines industry-leading AML risk intelligence with actionable risk signals to screen customers and monitor their behavior in near real-time.
Get a demoOriginally published 04 February 2025, updated 11 February 2025
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2025 IVXS UK Limited (trading as ComplyAdvantage).