Speed up your payment screening without compromising on risk.
Find out how ComplyAdvantage is helping financial institutions around the world.
Request a demoDespite being one of the most important lines of defense for financial institutions (FIs), many businesses struggle to balance effective security with ease of use during payment screening. To help mitigate these challenges, this article will look at:
Payment screening is the process of analyzing, verifying, and validating every incoming or outgoing transaction. Its purpose is to understand the risk of impropriety or criminal activity in any given payment. By screening payments, FIs can rapidly decide whether to escalate a potentially illicit transaction or allow a legitimate payment to go through.
This allows firms to remain compliant with anti-money laundering and counter-terrorist financing regulations (AML/CFTF) worldwide while protecting their customers and themselves from criminal attempts to siphon money or abuse payment rails. Because of this, FIs of all sizes must be able to screen every type of digital payment, from standard credit card transactions to faster payment schemes like FedNow and Instant SEPA credit. In our State of Financial Crime 2025 survey, 100% of businesses said they were confident about meeting SEPA requirements – but only with significant overhauls of their tech stacks and personnel.
Transaction monitoring refers to all the activities an FI undertakes to observe, record, and respond to customer interactions with its services. Transaction screening looks at individual transactions, such as payments, before they’ve been approved to stop especially high-risk activity. Payment screening is a facet of transaction screening, but it only deals with payments before they are processed.
Each screening process involves similar steps but can vary based on the specific risk factors involved in the transactions being screened.
Payment screening is necessary because FIs worldwide are subject to many regulations and recommendations to tackle criminal activity like money laundering, terrorist financing, and fraud.
These regulations vary between jurisdictions, but they invariably require that firms demonstrate a capacity to monitor and screen payments. Prominent regulations include:
Some common issues to look out for when processing payments include:
An effective payment screening process involves coordinating several different components. These include:
Once the initial payment message has been sent or received, the payment screening process begins. The diagram below details how ComplyAdvantage’s payment screening solution works, and the process can be broken down into five distinct stages.
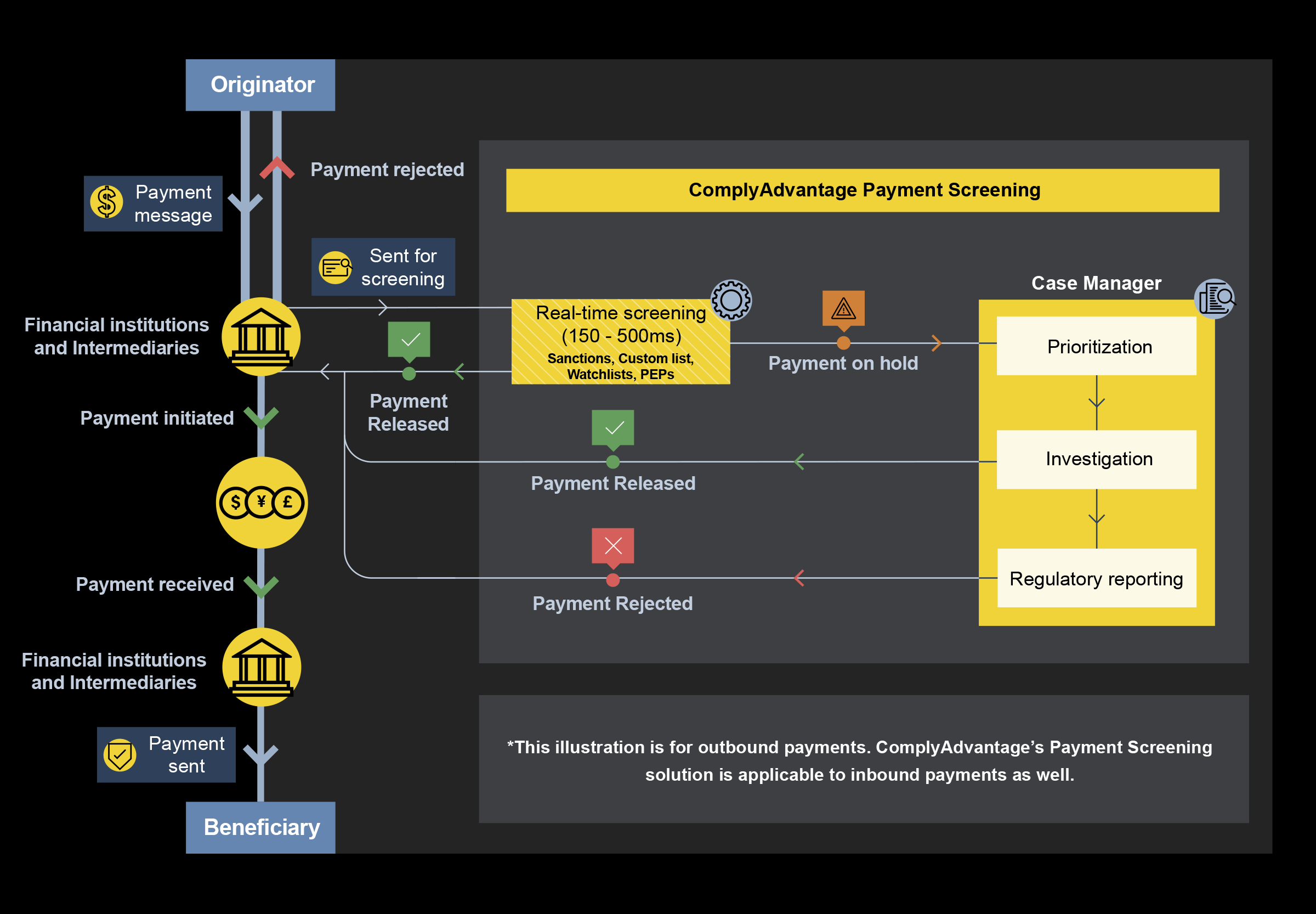
During the initial stage of a transaction, it is essential to gather all relevant data related to the payment message for validation. This includes the transaction amount, information about the sender and receiver, their respective locations, and any other essential details required for the payment to proceed smoothly.
Similarly, it’s important to verify the authenticity of the customer credentials to ensure that only legitimate transactions are processed. Therefore, both sets of data need to undergo a rigorous authentication process backed by robust technology and security protocols to minimize the risk of fraudulent activities.
Next, a risk assessment needs to be conducted to determine the probability of criminal activity based on the various degrees of customer due diligence outlined in the firm’s risk-based approach and how they apply to the specific customer in question.
This involves an evaluation based on the customer’s previous patterns of transacting, generalized patterns in historical data that indicate crime, the jurisdictions in question, and any other notable suspicions.
Then, businesses need to scan sanctions lists, watchlists, and politically exposed person (PEP) lists (maintained by regulators worldwide) to identify potential matches with the sender, receiver, or related organizations.If the payment is legitimate, these initial checks should take only a few milliseconds. However, if there is any indication of illegitimacy, then the case must be escalated.
If any of the preceding three stages raises a red flag that warrants further review, businesses will then escalate the payment in question to a dedicated team that specializes in conducting enhanced due diligence (EDD) processes. If this specialized team agrees that the payment is suspicious, it may be declined at this stage. However, after further review, the payment may be approved for processing.
Finally, if a payment, sender, or receiver is flagged as suspicious, the firm needs to supply the corresponding documentation to the relevant authorities immediately.
More importantly, businesses also need to maintain regular and detailed records of all these stages regardless of the outcome of any investigation for auditability and collaboration with regulators.
Payment screening helps FIs overcome some serious risks. However, given the complexity of all the moving pieces involved in these procedures, it brings unique challenges, including:
Given these challenges, firms must leverage advanced applications of technology like artificial intelligence (AI) and machine learning (ML) to automate and scale aspects of their AML payment screening processes. By automating fundamental steps like customer authentication and sanctions screening, firms can come closer to that necessary balance between speed and security.
Even when cases are escalated and need manual review, software can play an integral role in providing compliance teams with an intuitive workflow for rapidly managing anomalies.
Similarly, software can help teams document the necessary parts of each screening process so that they don’t have to undertake additional retrospective effort when reporting to regulators.
FIs of all sizes rely on ComplyAdvantage for intelligent, swift payment screening at scale. The platform uses a proprietary search matching algorithm to extract the full name and date of birth (if available) of the entity to be screened against an up-to-date and human-validated sanctions database. Firms can customize the payment screening platform to screen any entity, not just the counterparty, as long as a unique identifier is provided.
Among the top benefits experienced by firms using Payment Screening by ComplyAdvantage include:
Find out how ComplyAdvantage is helping financial institutions around the world.Speed up your payment screening without compromising on risk.
Originally published 04 March 2024, updated 21 January 2025
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2025 IVXS UK Limited (trading as ComplyAdvantage).