

Payment fraud is when someone steals another person’s payment information – or tricks them into sharing it – to make false or illegal transactions.
The 2022 AFP® Payments Fraud and Control Survey reports that 71% of organizations were victims of payment fraud attacks/attempts in 2021, costing businesses billions of dollars globally.
Customers must trust that their money is in safe hands. But one of the most challenging aspects of recognizing and tackling payment fraud is the complexity of the interconnected networks that underpin it.
Payment fraud: Part of a broader ecosystem
To understand payment fraud risks, it’s important to situate the typology in its broader context. Payment fraud is committed within a broader ecosystem of crimes. It depends on previous offenses (such as identity theft or data breaches) to occur. After it’s been committed, it often becomes a predicate offense to money laundering or is used to fund further criminal activity.
Payment fraud – A predicate offense for money laundering
The EU has identified fraud as one of the 22 key predicate offenses leading to money laundering and terrorist financing (ML/TF). Therefore, to understand payment fraud, it’s equally necessary to understand the ML/TF crimes that often follow it. This is crucial to grasping how payment fraud risk feeds into firms’ anti-money laundering and countering of terrorist financing (AML/CFT) risks.
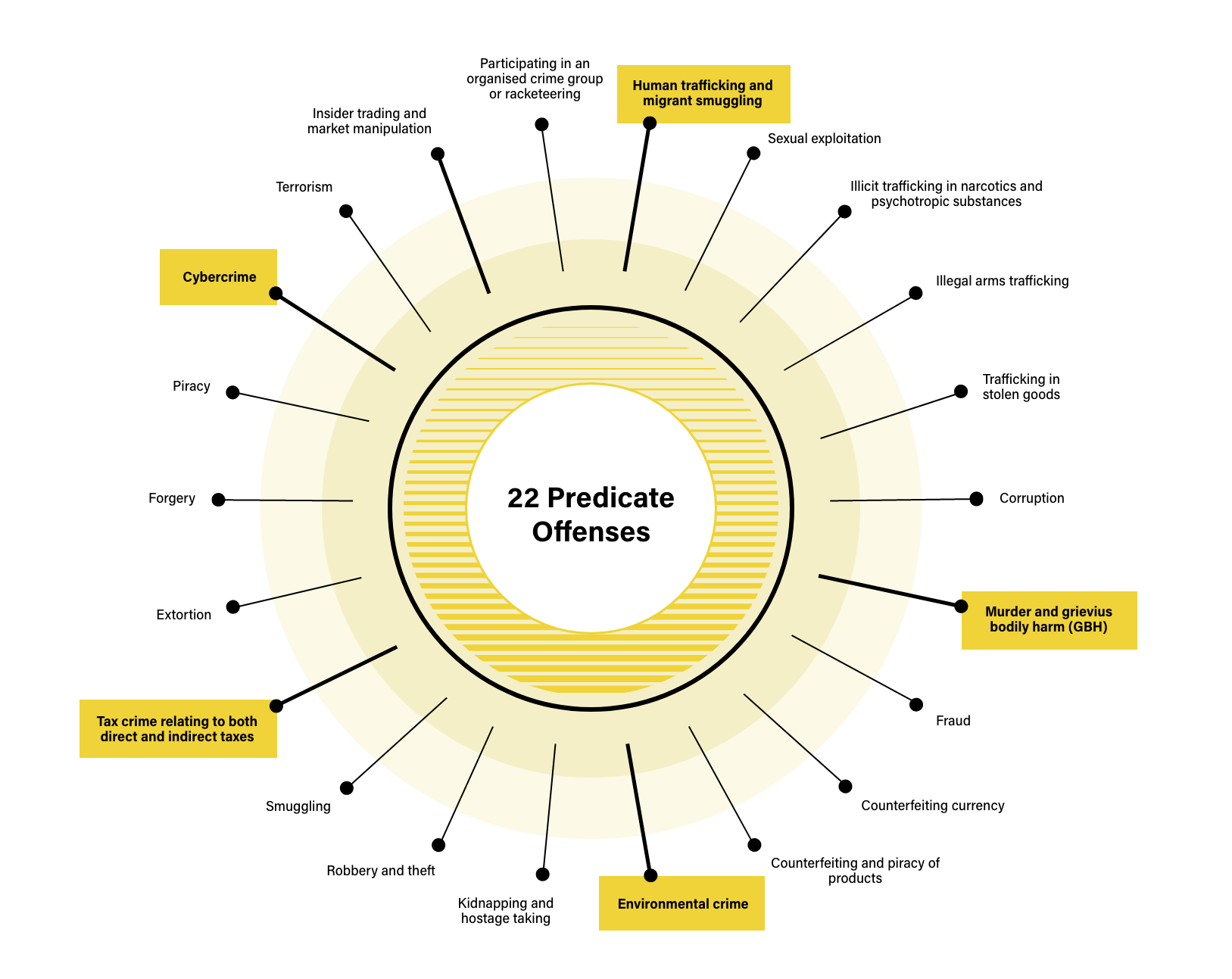
Laying the groundwork – Data theft
In order to commit payment fraud, criminals rely on the theft of personally identifiable information (PII). Although some types of transaction fraud depend on guessing or forging this information, obtaining it directly is a straightforward way to successfully execute a fraud event. The fraudster can use this information to commit identity theft – or even forge a synthetic identity out of a blend of PII – which then facilitates subsequent fraud schemes. Although data theft is a crime that often leads to fraud, it does not constitute fraud on its own.
Some of the most popular methods for obtaining this information rely on social engineering – using deceptive tactics to trick people into divulging information they normally would protect. By means of fraudulent emails, texts, calls, or web and social media pages, phishing convinces its victims to divulge sensitive data, download malware (such as ransomware), or even send funds. Its variations have earned a range of nicknames, including smishing (SMS scams), vishing (phone scams), whaling and spear phishing (targeting specific groups of people), and pharming (website impersonation).
At times, this information may be obtained by other means – sometimes aided by phishing – such as point-of-sale (POS) hacks and other data breaches. One of the more pernicious types of data breach is an Advanced Persistent Threat (APT) attack, which involves infiltrating a network to engage in illegal data mining. Distributed Denial of Service (DDoS) attacks, while not themselves data breaches, can provide cover for them.
Types of payment
The two main categories of payment types are card-present (CP) transactions and card-not-present (CNP) transactions. Despite the self-explanatory terms, these payment types are identified by more than the physical presence of a debit or credit card.
Card-present (CP)
CP transactions occur when electronic payment data is captured in-person, at the time of sale. This includes cards that are physically swiped via a card reader or digital wallets that are tapped on a contactless-enabled terminal. Examples include point-of-sale (POS) systems, card readers connected to tablets or smartphones, and contactless payments such as Apple Pay.
Card-not-present (CNP)
CNP transactions occur when the data on a card’s magnetic strip or chip is not provided with the transaction. CNP transaction methods include online shopping carts, subscription billing, phone orders, and payments on apps or smartphones that don’t require a card reader.
Types of payment fraud
After obtaining sensitive data, a fraudster can exploit it with various transaction fraud schemes. Though in-person fraud can and does occur, more schemes are remote – part of the global digital fraud trend.
CP fraud occurs through the use of stolen credit and debit cards, cloned cards, or cards that were applied for fraudulently. Given the accessibility of fake IDs, this type of fraud can be difficult to spot in the moment, relying on legitimate cardholders making a report.
CNP fraud occurs when a customer does not physically present a bank card during the fraudulent transaction. With the rise of digital payments, this type of fraud represented 80% of all card fraud as of 2019, according to the European Central Bank’s Seventh Report on Card Fraud. It can take multiple forms, including:
- Fraudulent payment at point-of-sale (POS) – The fraudster convinces the clerk to manually key payment information in for a card they do not have with them. Manual entry creates a force-posted transaction, which bypasses the normal authentication checks required in a standard card transaction. The transaction will go through even if there are not sufficient funds and may even bypass security measures for a card that’s been reported stolen – leaving the merchant vulnerable to chargebacks for breach of terms.
- Fraudulent payment online or over the phone – The fraudster submits payment information as though they were the true card owner. This is sometimes known as a carding attack when it’s done via a rapid-fire, automated process. If the transaction is executed without flagging transaction monitoring, the act can go undetected unless the actual account holder reports it.
- Prepaid card fraud – Stolen payment information is used to activate prepaid cards, which are often anonymous or low-security. This is a popular carding fraud target and can involve multiple automated orders at once. Alternatively, a scammer may activate the cards without paying by tricking a store clerk over the phone (vishing) or in person.
- Bank Identification Number (BIN) attacks – This is an example of a type of payment fraud that doesn’t require the theft of PII. In this case, fraudsters use a Luhn algorithm and other tactics to automatically generate and test a series of possible card numbers by attempting transactions until valid cards go through. This is partly based on publicly accessible BIN lists.
Outside of CP and CNP fraud, several other schemes are worth noting. Some of these methods are on the rise. They include:
- Authorized push payment (APP) fraud – In this scheme, a fraudster uses phishing tactics to trick a customer into authorizing a real-time payment to an account controlled by the fraudster. In 2021, APP fraud rose by 40% in the UK, accounting for 44% of all fraud as compared to card fraud, which sat at 40%.
- Account takeovers – In short, this involves an account being hacked such that the fraudster has direct access to funds that are not theirs. In the case of bank and credit card accounts, this allows them to request replacement cards to use physically. But other accounts can be hacked, including peer-to-peer payment and crypto accounts.
- POS cloning – This involves duplication of a merchant’s real payments terminal to allow the fraudster to commit illicit transactions. These may include fraudulent returns, as detailed in a report by Visa.
- Refund and chargeback fraud – Consumers fraudulently attempt to secure a refund through the chargeback process by contacting the merchant directly. This is sometimes known as “friendly fraud.”
- Advanced fee and wire transfer scams – In this scheme, fraudsters target victims to make upfront or advanced payments for goods or services that do not materialize. This can include career opportunity scams and psychic scams
Additional kinds of payment fraud involve digital wallets, double-dipping, and triangulation fraud. These and other schemes expose customers and firms to risks that are important to evaluate and mitigate.
How to detect and prevent payment fraud?
Having established the interconnected nature of payment fraud – including how it can contribute to money laundering and terrorist financing – firms can better consider how to incorporate this understanding into an effective risk program.
What is payment fraud’s place in a firm’s wider risk management system? Here’s how to think about payment fraud as part of a holistic risk and compliance framework.
1. Update risk assessments
A regularly-updated, company-wide risk assessment is crucial for a solid AML/CFT program – as well as for fraud prevention and mitigation. ACAMS includes fraud risk in its comprehensive AML-based risk assessment for firms, and the Australian government considers it so important that it’s published a comprehensive fraud risk assessment guide for firms. Given fraud’s status as a predicate crime, it’s critical to ensure all risk assessments are updated to include fraud risks, anti-money laundering, and terrorist financing risks.
2. Recognize red flags
Once a reliable risk assessment has been performed, fraud and risk teams will be better equipped to evaluate relevant red flags in line with their firm’s risk appetite. Although risk indicators are highly contextual, and often rely on a combination of other factors to establish high risk, there are some general areas of concern to be on the lookout for. Warning signs to bear in mind include behavior deviations atypical for a customer profile, such as:
- Shipping addresses too far from an IP address
- Atypical transaction amounts, volumes, or velocities
- Atypical transaction types or merchant categories
- ID document or other PII discrepancies
- Transactions exceeding the account balance or credit limits
- Unusual cross-border transactions
- Repetitive refunds or chargebacks
3. Implement effective measures
A risk-based approach built around customer profiles, security, and payment flows is key to a robust payment fraud risk-mitigation program – alongside employee and customer awareness of red flags.
Proactive KYC and customer due diligence can help firms better understand their customers, but managing payment fraud risks needs to take place at every stage of the customer journey and throughout firms’ functions, from back-end to customer-facing.
Online payment fraud, in particular, is dynamic and will keep changing as criminals access new technology and techniques to circumvent controls – and firms need to be able to detect changing tactics.
Alongside encryption of transactions, regular changing of login credentials, and the use of up-to-date software, there are other measures that firms should consider:
- Integrate biometrics and advanced identity verification (IDV) solutions during onboarding. Face, voice, fingerprints, or even veins in the hand or eyes, can enable strong authentication. However, consider if the technology is user-friendly, cost-efficient, and can be integrated into the broader KYC process.
- Dynamic transaction monitoring solutions can monitor risks in real-time, with practical case management that helps analysts prioritize the most high-risk alerts.
- Optimize with artificial intelligence (AI). While firms have adopted machine learning to automate processes, many are not optimizing their ability to help detect and tackle payment fraud. AI overlays can enable alert prioritization by risk – reducing operational costs and false positives and processing large datasets more efficiently to help analysts detect fraud more quickly and effectively.
- Identify and complete regular training programs. Europol, for example, has organized courses on the forensics of payment card fraud. Topics include examining skimming devices, ATM logical attacks, and malware attacks.
- Share fraud intelligence and information on incidents amongst firms and regulators – and with AML/CFT compliance departments.
In our 2025 State of Financial Crime survey, we identified fraud among the top 3 predicate offenses of concern for firms around the world. Fraud’s connection to money laundering and terrorist financing is becoming so clear that some firms have begun to refer to fraud and anti-money laundering as FRAML.
This highlights the vital importance of close communication and cooperation between fraud and AML/CFT departments within an establishment – yet all too often, these departments’ data and communications remain siloed. To ensure seamless collaboration and mitigation of FRAML risks, firms should consider an approach that opens the lines of communication and embraces active collaboration between both departments.
Payment fraud success story: RealPage
Property management firm RealPage processes up to 100 million transactions annually across a portfolio of more than 19 million properties worldwide. As a payments provider, it has a regulatory obligation to monitor transactions through its payment product, to ensure property management companies and their residents are effectively protected from illicit activity such as payment fraud.
RealPage needed a transaction monitoring solution that could screen for evolving fraud typologies in near real-time. The ability to do this using custom scenarios not used by traditional financial institutions was key. Effective case management was also critical to enable analysts to manage and triage alerts effectively.
To find out more, read the full RealPage story.
Request a Demo
See how 1000+ leading companies are screening against the world's only real-time risk database of people and businesses.
Demo requestOriginally published 26 July 2022, updated 22 January 2025
Disclaimer: This is for general information only. The information presented does not constitute legal advice. ComplyAdvantage accepts no responsibility for any information contained herein and disclaims and excludes any liability in respect of the contents or for action taken based on this information.
Copyright © 2026 IVXS UK Limited (trading as ComplyAdvantage).
